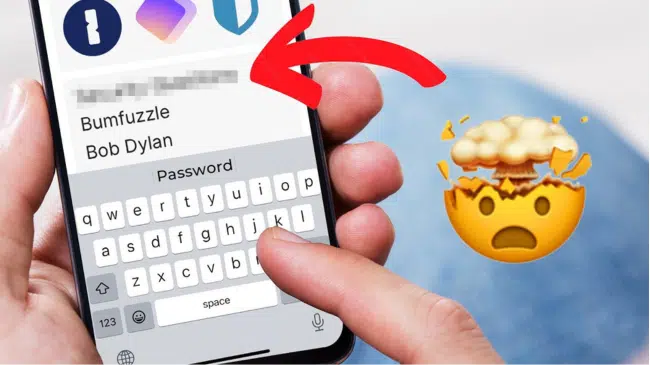
A password manager is an excellent tool for organizing and protecting your online accounts, but only if you know how to use a password manager effectively. Many people underestimate the security that password managers offer. If you’re serious about keeping your data safe, here are six crucial password manager best practices you must implement immediately. […]
Online Security Tips
Welcome to some of the best personal online security tips you'll find anywhere on the web!
Scroll through our most recent articles here or you can follow our step-by-step cybersecurity start page. My hope is that you'll be able to use these cybersecurity tips to lock down your online accounts, create better passwords, and browse the internet more securely.
You don't have to be tech-savvy and you don't have to spend a lot of money. These tips from All Things Secured can be done in just a few minutes or less and can make a drastic difference in your overall security and privacy online.
So what are you waiting for?!
Start browsing these online security tips NOW!
⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓⇓
How to Search Anonymously in 2025 Using Startpage (4 Pro Tips!)
Without even thinking about it, we type SO MUCH personal information into this tiny little rectangle known as a search bar. But what if there were a way to search anonymously? In this tutorial, we’re going to explore some free and simple ways to do more private searches online. There are so many different reasons […]
How to Ensure Your Phone Number Privacy in 2025
Your phone number shouldn’t be public knowledge. Spam calls and unwanted texts to your mobile phone number shouldn’t be an issue. If you want to learn how to hide your personal phone number, here are a few strategies you can use that are so easy you’ll wonder why you didn’t start doing them earlier. If […]
Defeat Email Phishing Scams in 2025 Using the STOP Method
Email phishing scams are often the biggest threats to our personal online security. And yet most of the time we ignore them because we think we’re too smart to fall for them. Watch out! The best way to defeat email phishing scams is to be alert and prepared…but how do you do that? Using the […]
7 Free Online Security Tools for 2025 You NEED to Use NOW!
Despite all the marketing we’re being fed, protecting your online privacy and digital security doesn’t have to cost you hundreds of dollars a month. These 7 free online security tools are what I recommend to protect you from online identity theft and hacking. I’ve said this before, but it’s worth saying this over and over […]
What is a Double Blind Password? Password Manager Hack 2025
Double blind password refers to a secure way to store passwords within a password manager app that keeps the real password hidden from both the app and the user. This method is a recommended solution for those who want the convenience of a password manager app without the potential risks of a security breach. The following […]