Yubico, a leading name in hardware security keys, recently acknowledged a vulnerability discovered in some of their products, sparking concern in the cybersecurity community. The issue lies in the cryptographic library used in YubiKey 5 Series and Security Key Series devices with firmware versions prior to 5.7.0. The vulnerability has raised questions among users, but here’s what you need to know about the risk level and whether it’s still safe to use a Yubikey 2FA security key.

We’ll break this down into three parts:
Let’s start with the security concerns, which are absolutely valid.
Valid Concerns: Physical Access and Advanced Attacks
The vulnerability stems from a flaw in Infineon’s cryptographic library, which was discovered by Ninjalabs and used in Yubico products before firmware 5.7.0 (any new Yubico key is not affected). This flaw could potentially allow an attacker to extract private keys from a compromised device.
However, for this attack to be successful, the attacker must have physical access to the security key, and the attack would need to be both sophisticated and targeted. Yubico’s official statement describes the issue as a “moderate” risk due to the high level of difficulty in executing the attack.
While it is understandable that users may be concerned about this flaw, it is important to remember that this is not a vulnerability that can be exploited remotely or easily. Physical access to the device is required, and the attack involves specialized equipment and knowledge. Still, Yubico users should take this issue seriously and be aware of their key’s firmware version.
Yubico’s decision not to allow firmware upgrades has been a point of discussion for some time, and this latest vulnerability has led some to question whether this policy leaves users exposed to risks. However, Yubico maintains confidence in this design decision, and understanding these reasons can help users feel more confident in the security of their devices.
Why Yubico Doesn’t Allow Firmware Upgrades
Unlike many other hardware products, Yubico does not allow firmware upgrades on their security keys. At first glance, this might seem like a flaw in their design, especially in light of recent security vulnerabilities. However, this decision is grounded in an important security principle: reducing the attack surface.

Allowing firmware upgrades would introduce the risk of malicious firmware updates. If a malicious actor could push a fraudulent firmware update to a YubiKey, they could compromise the device without even needing physical access. By preventing firmware upgrades, Yubico ensures that no external party can alter the device’s core functionality once it leaves the factory. This is a trade-off that favors long-term device integrity over short-term flexibility.
This security-first design approach, while it might seem restrictive, actually enhances the overall security posture of the devices. While the current vulnerability is unfortunate, Yubico’s focus on minimizing potential future risks is commendable.
5 Reasons Why You Shouldn’t Worry
Despite the concerns surrounding this vulnerability, Yubico keys remain some of the most secure authentication devices available. We still recommend you use a good 2FA key to secure your online accounts and continue to use these keys ourselves.
Here are five reasons why you shouldn’t be overly concerned about this vulnerability:
1. The Attack Requires Physical Access to the Key
For this vulnerability to be exploited, an attacker must physically possess your YubiKey. Remote attacks are not possible, which drastically reduces the likelihood of this vulnerability being exploited in real-world scenarios.
While physical theft of your key is always a concern, the reality is that most users are unlikely to lose their security keys or have them stolen by a highly motivated attacker.
2. The Attack Requires Expensive Equipment ($11,000+)
Even if an attacker were to gain physical access to your key, they would need specialized equipment valued at around $11,000 to execute the attack. This equipment is not easily accessible or affordable for the average hacker.
The high cost and complexity of the attack make it highly unlikely to be used on a wide scale. It’s much more probable that an attacker would simply try to steal the key and use it directly, rather than attempt to duplicate it.
3. A Copied Key Secured with a PIN Still Requires the PIN
Yubico devices offer the option to secure the key with a PIN (which is encouraged). Even if an attacker were able to duplicate your key using the vulnerability, they would still need to know your PIN to use it. Without the PIN, the duplicated key is useless, providing an additional layer of protection.
This is especially relevant for users who utilize YubiKeys in environments where high security is necessary, such as accessing corporate networks or managing sensitive personal data. It’s worth noting that when using a Yubikey as a passkey, creating and using a PIN is required.
4. Yubico Firmware 5.7 and Above Are Not Affected
Yubico has already addressed this vulnerability in its latest firmware update (version 5.7.0 and above). This means that users with newer YubiKeys, or those who upgrade to a device with the latest firmware, are not at risk from this particular issue.
Yubico has also removed its reliance on Infineon’s cryptographic library in newer devices, opting to use its own library instead. This shows the company’s commitment to improving the security of its products and responding to vulnerabilities promptly.
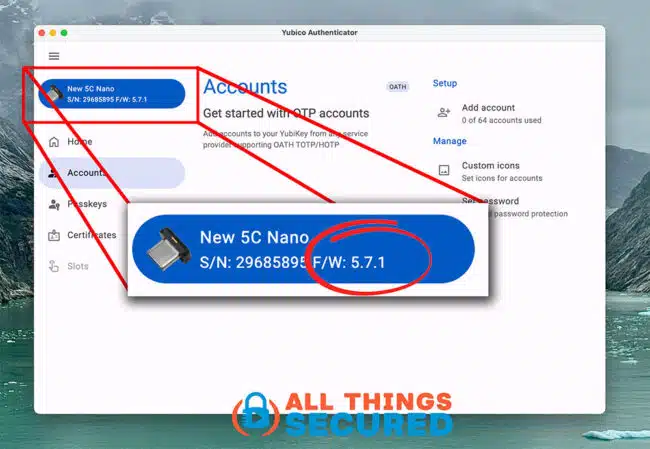
To check the firmware of your key, download the desktop or mobile app, plug in your key, and find the firmware used.
5. This Is No Different Than Someone Stealing Your Key
At its core, this vulnerability is functionally no different than someone physically stealing your key. In both cases, the attacker would need to possess the key to exploit it.
Most security practices involve safeguarding your key to prevent theft, and the same measures apply here. For an attacker to successfully exploit this vulnerability, they would need to directly target you, already know your username and password, steal your key, and perform a complex and expensive attack.
The reality is that this is highly unlikely for most users.
Are Yubikeys Still Safe to Use?
Yubico’s hardware security keys have long been regarded as a critical part of cybersecurity and this recent vulnerability does not change the fact that they are still the most secure method for protecting online accounts.
While the discovery of this flaw in older firmware versions is concerning, the practical risk to users remains low due to the complexity and cost of the attack, as well as the requirement for physical access to the device. Additionally, Yubico’s decision to disable firmware upgrades is rooted in a desire to protect users from future risks, and newer devices with updated firmware are already available.
If you are using a Yubico device with firmware older than 5.7.0 and you’re concerned about this vulnerability, consider upgrading to a newer model. But even without upgrading, your YubiKey remains a highly secure device, and the likelihood of this vulnerability being exploited is minimal.
In a world where cybersecurity threats are constantly evolving, Yubico continues to prioritize security and stay ahead of potential vulnerabilities. With good security hygiene and awareness, users can continue to rely on their Yubico keys for robust protection.




