In an era where online security is increasingly critical, traditional usernames and passwords are facing stiff competition from a new security standard known as passkeys. This standard has proven quite confusing however. Are passkeys more secure than 2FA? Do passkeys replace passwords? In this article, we will dive deep into what passkeys are, how they work, and whether they are worth adopting for your online security.

In order to fully appreciate passkeys as a new security standard, it’s important to examine and understand the old standard that has brought us this far. We’re going to cover:
- The Evolution of Online Security (Passwords)
- How do Passkeys Work?
- Two Types of Passkeys
- Passkey Adoption and Challenges
- Should YOU Use a Passkey?
- The Future of Passkeys
Let’s dive in!
Evolution of Online Security: Passwords to Passkeys
Passkeys are nothing more than an iteration on decades worth of online security. There’s a lot that we’ve learned from our current models, which begin with passwords.
The Problem with Passwords
The concept of passwords dates back to the 1960s when MIT researcher Fernando Corbató introduced a password system to allow multiple users to access a single computer securely. While his initial system was extremely simple, over the decades, the process has been refined with techniques like password hashing, salting, and multi-factor authentication (there’s a difference between 2FA and MFA).
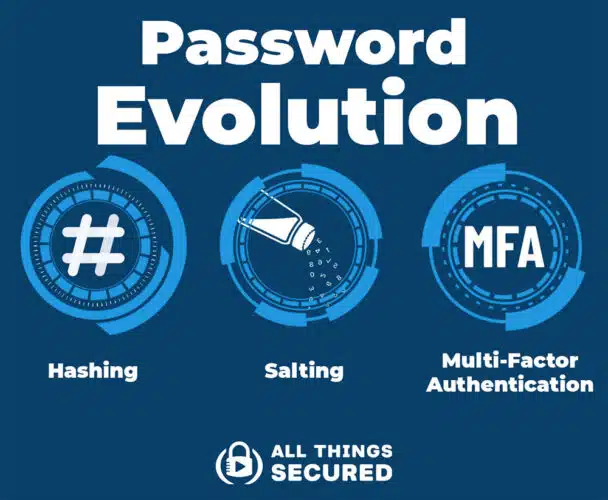
There’s still a fundamental problem, however: passwords are a shared secret between the user and the service provider.
This shared secret is a significant vulnerability.
If a hacker gains access to the database where these passwords are stored (and these breaches happen all the time!), they can potentially access millions of accounts. Despite advancements like two-factor authentication (2FA), which adds a layer of security by requiring something you have – like a phone or security key – or something you are – like a fingerprint – passwords still pose a considerable risk.
The Next Generation: Passkeys
Passkeys represent a revolutionary approach to online security by eliminating the need for shared secrets. Instead of relying on a password that can be stolen or hacked, passkeys use a public-private key pair to authenticate users. This method separates the digital “padlock” (public key) from the “key” (private key), making it nearly impossible for hackers to reverse-engineer the login credentials.

The private key, typically secured by biometric data such as a fingerprint or facial recognition, is never shared with the service provider. This makes passkeys not only more secure but also more convenient since users no longer need to remember or enter complex passwords.
How Do Passkeys Work?
The typical username/password combination is pretty easy to understand. Passkeys, unfortunately, aren’t nearly as simple. This is likely one reason why general public adoption has been slow. But let’s take a closer look at what happens when you use a passkey.
Public-Private Key Pair Explained
At the core of passkeys is the public-private key pair system, which is a common feature of modern cryptography. When you set up a passkey, two cryptographic keys are created:
- Public Key: This is the “padlock” that is shared with the service you are logging into. It is safe to share because it cannot be used to reverse-engineer your private key.
- Private Key: This is the “key” that remains securely on your device. It is used to unlock the “padlock” during the authentication process, and it is never shared with anyone.
When you attempt to log in, the service sends a challenge to your device, which is then signed by your private key. This signed challenge is sent back to the service, which verifies it using the public key. If everything checks out, you’re granted access.
This is, obviously, a very simplified explanation, but hopefully it helps you appreciate what’s happening in the background. There’s a lot of complicated math used to verify this public-private key pair.
Additional Benefits of Passkeys
In addition to being a more secure way to log into your accounts, passkeys are considered better than passwords for other reasons as well.
- Phishing Resistant: Passkeys are tied to specific accounts, which means they can only work with the website on which they were created. Even if a malicious actor tried to get you to sign in on a fake website to steal your data, a passkey wouldn’t work.
- Spy Resistant: It is possible to use a passkey with somebody looking over your shoulder without giving away any secret. A keylogger could be secretly installed on your device and a passkey wouldn’t be compromised like a password would.
- Convenience: A passkey promises to be much more convenient to use since it only requires a single point of verification instead of inputting a username, password, and then 2FA. In most cases, this single point of verification is biometrics.
The Role of Biometrics
Most passkeys are secured by biometric data, such as a fingerprint or facial recognition. In other words, when you use a passkey, you’re likely going to be asked for FaceID or a fingerprint scan on your device.
This adds a layer of security because even if someone were to gain access to your device, they would still need to replicate your biometric data to use your passkey. This method is both secure and user-friendly, as it eliminates the need for entering passwords or codes that you have to remember..
Types of Passkeys: Syncable vs. Single-Device
Understanding the different types of passkeys is crucial for optimizing your online security. There are two main types of passkeys: syncable and single-device.
Syncable Passkeys
Syncable passkeys are those that can be synced and used across multiple devices.
For instance, if you create a passkey on an Apple device, it can be synced across all your Apple devices through iCloud. This means you can log in from any of these devices without needing to create a new passkey for each one.
While this is incredibly convenient, it does introduce a slight risk because the passkey is stored in the cloud. If your cloud account were compromised, someone could potentially access your passkeys. However, since they still need to authenticate using biometrics or a master password, the risk is still significantly less than if somebody were to hack a database with your password.
Single-Device Passkeys
Single-device passkeys, on the other hand, are stored only on one device and cannot be copied or synced to another device. This type of passkey is ideal for highly sensitive accounts where security is paramount. For example, you might use a single-device passkey for your financial accounts or other sensitive information.
Here’s an example of all the passkeys that are stored on my Yubikey:
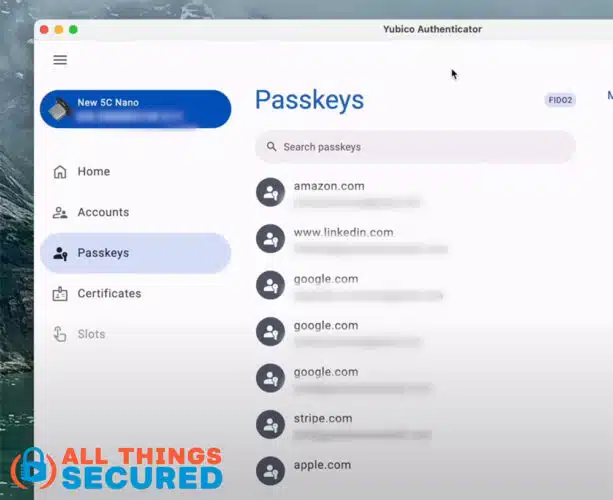
The passkeys stored on the Yubikey cannot be copied anywhere else and in order to use the passkey, the device has to be plugged into or tapped onto the computer or mobile phone.
The downside is that if you lose the device, you lose access to the passkey, which could be catastrophic if you don’t have a backup. Many users mitigate this risk by creating a backup passkey on another device and storing it securely.
Current State of Passkeys: Adoption & Challenges
Despite the advantages of passkeys, their adoption has been slow. While tech giants like Google, Apple, and Microsoft have started implementing passkeys, many online services still rely on traditional username-password-2FA systems.
You can take a moment even now to check out this passkeys directory to see how many services that you use on a daily basis offer passkey support. Chances are, you’re going to be surprised by how few opportunities you will have to use them.
This means that for now, passkeys are not fully replacing passwords but are being used alongside them.
For instance, when logging into Amazon with a passkey, users are still required to enter their email and may even need to input a 2FA code. This raises the question: if passkeys are not simplifying the login process, what’s the point?
Should You Use Passkeys?
The short answer is yes—passkeys offer a more secure and often more convenient way to protect your online accounts, even if there aren’t many places that you can use them right now. However, the question of how to use passkeys is more nuanced.
For Less Sensitive Accounts
For accounts that do not contain sensitive information, such as streaming services or news sites, syncable passkeys are a great option. They provide convenience without requiring the user to manage multiple passkeys across devices.
Why not just continue to use username and passwords? Well for one, it’s good to get into the habit of using higher forms of account security where possible. But as we discussed earlier in the additional benefits of passkeys, using them is an active way to prevent phishing and spying.
For Highly Sensitive Accounts
For accounts that hold sensitive personal data or financial information, a single-device passkey is the more secure option.
IMPORTANT! If you use passkeys for these kinds of accounts, you MUST create multiple forms of backup to be kept in secure locations. If you lose your single-device passkeys, it’s quite possible that you could lose access to your account.
While less convenient, it ensures that your passkey is not vulnerable to cloud-based attacks.
The Future of Passkeys: What to Expect
While passkeys are not yet ubiquitous, their adoption is expected to grow as more companies realize their security benefits. However, passwords are unlikely to become obsolete in the near future.
In the meantime, the best practice is to use passkeys where possible, especially for accounts that require robust security.
Balancing Security and Convenience
Passkeys represent a significant advancement in online security, offering a more secure alternative to traditional passwords. By eliminating the shared secret and leveraging public-private key pairs, passkeys reduce the risk of data breaches and make logging in more convenient. However, the balance between security and convenience varies depending on how you use passkeys.
For now, the best strategy is to adopt passkeys for your less sensitive accounts while continuing to use strong two-factor authentication for more critical accounts. As the technology matures and adoption increases, passkeys could very well become the standard for online security.
In summary, passkeys are worth considering as part of your overall security strategy. They offer significant benefits, particularly in terms of security, but the decision of when and how to use them should be based on your individual needs and risk tolerance.

