In November 2023, Proton Privacy launched a beta feature called “Key Transparency” that utilizes a private blockchain to verify that an email address belongs to the person you intend to communicate with. Despite being one of the most respected providers of data privacy products in the world, this is the first time that Proton has used blockchain technology as part of their service. Here’s an explanation of how it works.

Proton CEO Andy Yen described Key Transparency like this:
It’s an example where blockchain, from a technical standpoint, solves…a real problem in security and privacy.
According to Proton, this new Key Transparency feature takes encrypted email to the next level of security. But how does it work? And what makes this such a unique feature?
Although the math behind all of this is complicated, here’s an explanation that should hopefully make sense to you.
How Email Address Verification Works
The idea of secure email is that a person can send a message to anyone in the world knowing that only the intended recipient can open and read it. Proton Mail applies end-to-end encryption to the content of the email ensuring that nobody else can intercept and read the message.
This is done using what is known as public key cryptography, a system in which two keys – a public key and a private key – are generated for each user. The public key is, as the name suggests, public, while the private key is unique to each individual and should never be shared. The public/private key standard used by Proton is referred to as PGP or “Pretty Good Privacy.”
A simplified version of the process looks like this:
- An email sender chooses their recipient;
- If the recipient has published or shared their public key, this key will be used to encrypt the message;
- During encryption, the message is digitally signed using the sender’s private key;
- When received, the message can only be decrypted using the recipient’s private key;
- Once decrypted, the digital signature is checked using the sender’s public key;
If both the sender and receiver use Proton Mail, both can know with complete confidence that the public keys associated with each party are correct since Proton holds them both.
But outside of that protected ecosystem, there are ways in which bad actors can spoof an email address or create a fake public key linked to a particular individual. This is known as a man-in-the-middle attack and it basically allows others to copy the key that unlocks an encrypted email without either the sender or recipient knowing.
The problem to be solved is this: how can a particular address and public key be verified as actually being legitimate?
Key Transparency Using Blockchain
The answer to the problem would be some kind of tamper-proof database of public keys.
As Andy Yen puts is:
It’d be nice if there was a…read only ledger that recorded all the public keys in existence and no one can modify that ledger. Well, another word for that is a blockchain.
Such an immutable ledger could store all of these public keys to make it nearly impossible to fake or spoof, and that’s exactly what Proton aims to do with their new Key Transparency project.
Currently, the project is hosted on a private blockchain on Proton servers, but mass adoption would eventually require moving to a public blockchain. Because this blockchain is by nature decentralized and cannot be altered, it would serve as the permanent record for everybody’s public keys.
You can already be confident that the contents of the email you’re sending are end-to-end encrypted with a service like Proton. With Key Transparency, you can now be sure that the address you’re sending to is actually the person you intend to communicate with.
How to Turn on Key Transparency in Proton
Turning on Key Transparency within your Proton account is a simple toggle switch.
Once you log into your Proton Mail account, click on Settings gear wheel on the top and click All Settings.
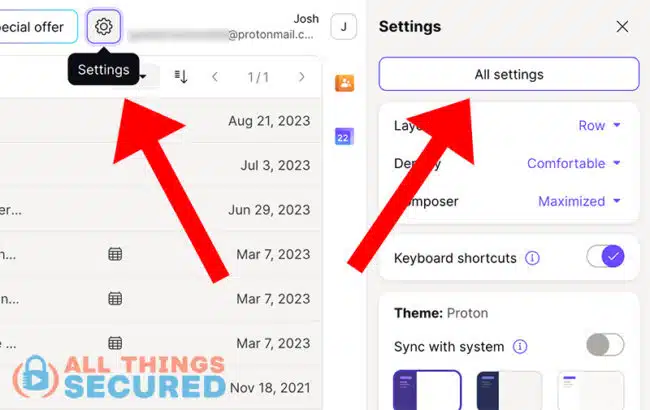
On the left menu bar, scroll down until you find Encryption and Keys.
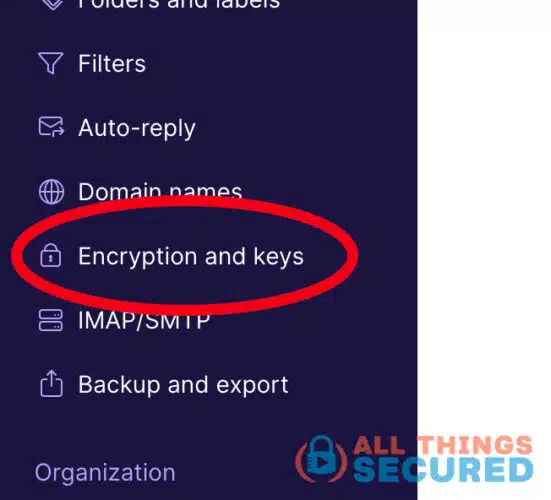
You want to make sure that you turn on Verify Keys with Key Transparency.
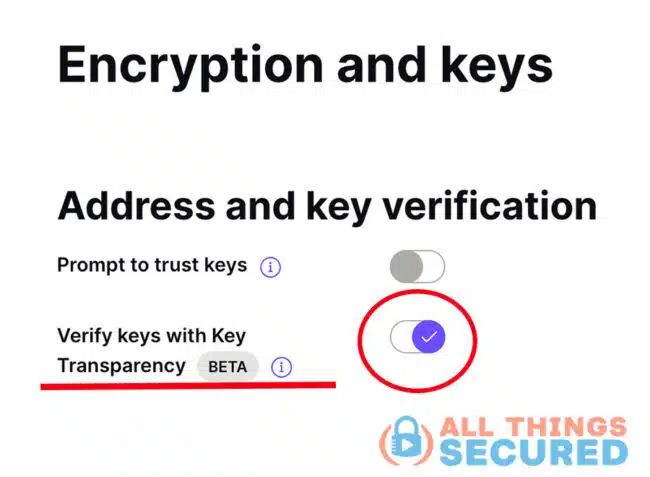
That’s it’s! Your public key is now stored on the Key Transparency blockchain and you will now automatically start checking the status of keys for those to whom you send email.
Further Reading
If this has been helpful to you, here are some other related articles you might find interesting:

