The biggest problem with using any virtual private network, or VPN, is simply trust. Can you trust this company with your most sensitive data? But what if trust wasn’t part of the equation? In this article, we’re going to explore how decentralized virtual private networks, or “dVPN” for short, might be a solution.

The Problem with Traditional VPNs
If you’ve read any of my VPN reviews here on All Things Secured or seen my videos on YouTube, you know that I have one big pet peeve about the VPN industry that I think is a concern:
We’re being asked to place our trust in these VPN providers, most of whom won’t tell us a single thing about who they are or who owns them.
If privacy is your primary concern, then when using traditional VPNs, it’s not that you’re using some magic technology that makes you completely anonymous.
You’re merely replacing your distrust of your…
….internet service provider…
…your network…
…your government…
…or whoever you’re worried might be snooping on your internet activity with trust in some random company that makes plenty of promises about security and privacy, but for all intents and purposes, has no accountability to those promises.
When you connect to a conventional VPN server, you’re rerouting all of your internet traffic through that centralized VPN. To make matters worse, in many cases these VPN servers aren’t even owned by the companies themselves, they simply rent the centralized servers from data centers.
A VPN isn’t a cloak of internet invisibility, it’s just a re-alignment of trust.
That’s where something like a decentralized VPN service begins to look enticing.
What is a Decentralized VPN?
What is a Decentralized VPN?
A decentralized VPN, or “dVPN” for short, is a peer-to-peer network of privately owned VPN servers that don’t have any centralized control since they aren’t owned or operated by any one company.
Taking a page from the blockchain playbook, decentralized VPNs take the power away from big, centralized VPN provider by giving it to a distributed network of private servers.
The end goal is to create what is known as a “trustless network” where users have a secure internet connection via encrypted protocols to individual nodes on the decentralized VPN network.
You’re taking advantage of their unused network traffic and they’re getting compensated in the process. This would eliminate the need to trust any one single VPN company with all your data.
What’s the difference between a decentralized VPN and TOR?
TOR vs dVPN | What’s the Difference?
This idea of a decentralized VPN network isn’t anything new. The Tor project, which was originally developed by the US Navy to protect their own intelligence communication, was released publicly in 2002.
Despite some pretty far-fetched conspiracy theories, most experts agree that although Tor isn’t perfect, it is a viable trustless network solution.
You see, Tor, which stands for “The Onion Router”, is best explained by its namesake, an onion. As data is passed through a volunteer network of relay servers, it’s almost like an onion of security.
- The first layer of security tells the first server, or node, what to do.
- Once this packet of data is sent along, the next layer of the onion is peeled away revealing the instructions for the next node;
- And so on and so on until it finally reaches its destination.
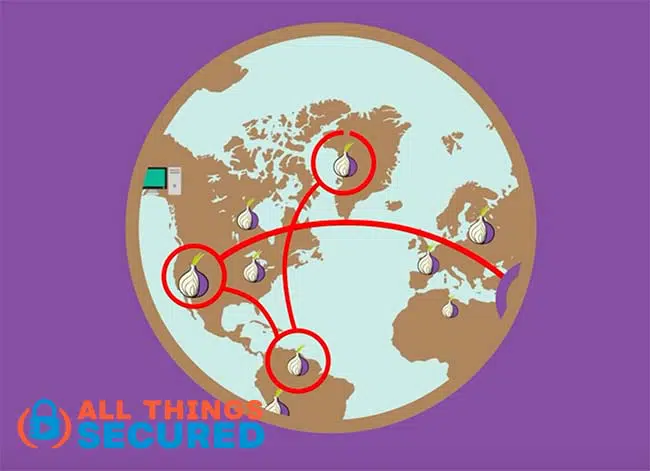
Since each node operates on a “need to know” basis, no one single node can see the whole story of who is sending what data where or even attempt to keep centralized logs.
But even Tor has its own limitations.
For example, all these layers of routing make for extremely slow internet speeds. The extra privacy and security measures only apply to internet activity done from within the Tor browser itself. It doesn’t cover any other app or programs on your computer or mobile device.
Also, your internet service provider can still see that you’re connected to Tor, and your exit node, which is where you leave the Tor network, can eavesdrop on the internet traffic even if it doesn’t know where it came from.
Connecting those two points is extremely hard, which is why Tor has been considered one of the best privacy tools available. But in some ways that makes decentralized VPNs safer.
What Decentralized VPN Solutions Exist?
So if a VPN provider requires too much trust and Tor is still open for eavesdropping, what options are there?
Well, first, you could run what’s known as a Tor over VPN, which simply means you’re connecting to a VPN and then running that connection through the Tor network.
Or…you could consider a dVPN. But how does a decentralized VPN work?
A decentralized VPN relies on the distributed power of a global network. For example, I’ve set up my Raspberry Pi 4 to run as a node when I’m not in the office, and it earns a little bit of cryptocurrency in exchange for sharing my unused bandwidth with other users around the world.
There are a couple of startups that are facilitating this new push towards a decentralized VPN, including Orchid and Tachyon, but the one I’ve been using is known as the Mysterium Network.
How a Decentralized VPN Works
The way that Mysterium – or any reliable decentralized VPNs work – I’m still using Wireguard or OpenVPN protocols to encrypt my data, but then that data is sent through multiple nodes until it reaches a specific exit node run by Myserium.
As a user, I pay these public nodes via cryptocurrency for the bandwidth I use, and for my Raspberry Pi, I receive crypto for the bandwidth I provide.
Best Decentralized VPN for 2024
The dVPN market isn’t crowded just yet, but I’m confident this will change in a few years.
However, there are a few “first mover” companies that have established a good reputation as a dVPN option, which include:
- Mysterium Network
- Orchid VPN
- Tachyon VPN
Here’s a look at each one of the best decentralized VPNs individually.
Orchid dVPN

- Multiple provider networks available;
- Accepts Crypto payments;
- Unlimited devices to connect;
Tachyon VPN

- Over 1200 nodes available;
- Crypto payment;
- Open-source project development;
dVPN vs VPN vs Tor | Which is Better?
A couple things worth noting here when it comes to the differences between a decentralized private network, regular VPN providers and Tor.
- Speeds: First, decentralized VPNs are very similar to running a VPN over Tor, except that it’s much faster and you can actually control your exit node, so you have the ability to unblock streaming content, which Tor doesn’t allow for.
- Blocking: dVPN is much harder to block because, unlike a VPN connection or a Tor connection, your data is running through residential IP addresses, such as with my Raspberry Pi here in my office. It’s like walking through a crowd of people in New York City…you just blend in.
- Router Configuration: If you want to set up security for your entire home network, both Tor and decentralized VPNs are almost impossible to use. That’s where you need to check out the best VPNs for routers, which can easily be configured for all your Internet of Things devices.
- Open Source: Decentralized VPNs, or at least the Mysterium Network that I use, uses an open-source code base that has been reviewed and audited. This is similar to Tor but entirely different from the proprietary system set up by VPNs.
- Payment: Decentralized VPNs run on a pay-as-you-go model, based on the amount of bandwidth you use. Tor is free while a VPN is a monthly or annual subscription model.
- Logging: Finally, since your data is running through a growing network of unaffiliated nodes, unlike with a conventional VPN, it’s technically impossible for any centralized logs to be kept through decentralized VPNs.
Is it Safe to Run a dVPN Node?
These security measures all fine and good, but I’m also fully aware that technology like this, even if it’s developed with good purposes in mind, is often used for unlawful or even immoral purposes.
You can’t throw the baby out with the bathwater, but as a person who runs a public node, I also don’t want to be complicit in criminal activity.
I asked Mysterium about this and their solution was interesting to me. They’ve combatted this in two ways.
First, as a node, I can choose to accept only whitelisted traffic, meaning my node will only route streaming services like Netflix, Pandora, Hulu, and others. This will limit my liability, but also limit my earning potential as a node.
Second, Mysterium takes on most of the liability by maintaining all exit nodes for the network. I only act as a relay, and theoretically at least, none of the traffic could be traced back to my relay node.
Final Thoughts on dVPN Technology
I’ve never been comfortable with the trust we place in the centralized structure of VPN services and I’m very interested in how blockchain technology could change that in the future.
We may still be using traditional VPN services like NordVPN or ExpressVPN going forward, but because of the work of decentralized VPNs like Mysterium, it could entirely change the way that privacy and encryption is run.
If you’d like to give a decentralized network a try, visit Mysterium.network and as you sign up, use the code “AllThingsSecured” to get free MYST for getting started. Enjoy!



Great article but WHy has this left out the biggest and the most developed dvpn project? Sentinel
Never used it before, I guess that would be the reason 🙂
Does it mean that Dvpn are multi hop vpns by default with the hops being community members instead of simply the main company?
Not always. You don’t have to multihop with a dVPN, but as you said, each node is a community member instead of the main company.
Do you know of any routers that use dVPN?
I found this post looking for an alternative to TOMATO + NORDVPN ON R700. But also realise a router upgrade might be needed.
Point being, I can’t find any dvpn router native options …
I don’t think there is one that I’m aware of. You can always just set up a Raspberry Pi right before your router, but I wouldn’t call that “native”.
Don’t know all of the details, but, take a look at Deeper network DPN as they can connect before and/or after your router,(I think). Worth a look.
Thanks, Doug. I will.
What is better for privacy protonvpn or mysterium vpn
Two different tools that depends on your needs.